If you follow the news at all, you’ve probably heard at least something about the WannaCry ransomware virus that has been making life miserable for IT and security professionals every since last Friday.
This malware is certainly the worst seen so far in 2017, and is one of the most quickly-spreading malware attacks ever, infecting around 57,000 computers in more than 150 countries within about 24 hours of being introduced.
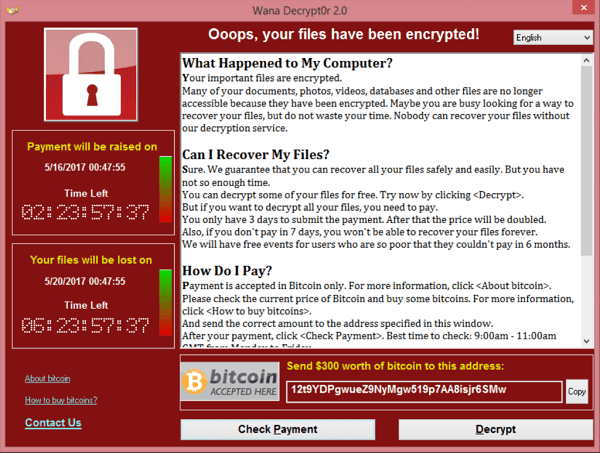
WannaCry is a ransomware trojan horse virus, meaning that it instead of outright destroying the computer it locks down and encrypts the contents of your hard drive and then forces the computer user/owner to pay a ransom in order to access their own files. If the ransom isn’t paid in time, then the virus will delete the user’s files.
While this has been incredibly devastating for large organizations (like Englands National Health Service and several large manufacturing companies) there are a few things that most people can do to keep themselves safe.
#1 Keep Your Operating System Updated
Most people and groups infected with this virus were running operating systems that were incredibly vulnerable.
The exploit used by WannaCry (which was originally found by the NSA and is known as EternalBlue) has been patched in all current Windows versions way back in March. Those hardest hit were running Windows XP (which Microsoft declared End of Life in April 2014), Windows Server 2003 (which was End of Life in July 2015), and Windows 8 (which was depreciated in favor of Windows 10).
Basically, if you’re an individual running one of these operating systems, the burden is on you to update it – MS supported both XP and Server 2003 for 12 years, and can’t be expected to provide indefinite support. However, Microsoft has patched this vulnerability due to the widespread nature of this attack, so if you are running XP, make sure that you download their patch, and then update your damn operating system!
Of course, many of the hardest hit organizations run XP or Server 2003 because they must. Hospitals, especially, have lots of proprietary software that was developed a long time ago and at great expense, and the software vendors – which may or may not still be around – would likely charge quite a bit to update their software to work with Windows 10.
Lots of equipment for hospitals and manufacturing also run Windows XP (ever seen a Windows error message on an ATM?) like the proprietary software, updating these devices to use a more modern version of Windows is either very expensive or not easily possible.
Of course, I imagine that this malware attack will have lots of people reconsidering these approaches for large organizations that use mission-critical (or life-critical) software.
#2 Be Aware of Phishing Emails
The ransomware component of this attack, although brutal, wasn’t how it first spread. This malware, like lots of viruses, uses a process known as “phishing” to find victims and spread itself.
Just about everyone who has an email address has likely seen a phishing email. Those emails that claim to be from your bank, or Paypal, or Google, with some sort of time-sensitive or important-sounding alert and a link that says “click here” are – 99% of the time – phishing emails.
These links either take you to a decent-to-good model of a login screen so they can steal your username/password OR take you to a site with some sort of malware.
The best (and really) only way to guard against phishing attacks is simple paranoia. When (not if) you get a suspicious and unexpected email that prompts you to login to a site don’t click the link in the email. Instead, enter the site address yourself in your browser (Chase.com, Paypal.com, for example). This will make sure you go to the correct domain and not a malicious site.
Lots of malware “in the wild” today are zero-day exploits. This means that the vulnerability being exploited isn’t known to software companies until it appears, and so OS updates, antivirus or firewall software won’t protect you. The best way to protect yourself is diligence!
Small aside – one company I do freelance work for, Ironic Design, has a system called Email Security Training which is designed to train you (and family/employees/whoever) how to spot these phishing attacks and protect you, your network, and your business!
#3 WannaCry Stopped – Kind Of
One of the neatest parts of this whole saga is a security researcher that accidentally stopped the spread of the WannaCry virus in its tracks – at least temporarily.
You can read the whole, nerdy saga at Ars Technica, but the short version is that while inspecting the code of the virus, he noticed that it was trying to connect to a specific domain that was unregistered.
While attempting to gather data on the spread of the malware infection (since each infected computer would try to contact this unregistered domain) the security research registered it. After a bit of panic that registering the domain had caused all the computers infected to be immediately encrypted, it became obvious that this domain was essentially a kill switch.
This means that the original malware would cease to function – however, this didn’t unencrypt any files that were already encrypted. This success will likely be shortlived, though, as it is a relatively trivial task for the malware creator to change the URL for the killswitch or just remove the kill switch functionality altogether.
Like I said – update your computer!

Leave a Reply
You must be logged in to post a comment.