I mentioned a couple of weeks ago that some Chinese-made Android phones may contain invasive (or insecure) software from the factory.
But a new study has looked at the security of Android OS (and variants developed by several companies) and found some troubling data collection practices that are “baked-in” to the OS itself, with no way to turn them off.
The Manufacturers
The study, which was carried out by researchers from the University of Edinborough and Trinity College, covered the following phone OEMs and Android variants.
- Samsung
- Xiaomi – covered in my previous article
- Huawei – also covered in my previous article
- Oppo/Realme (One of Oppo’s subsidiaries is OnePlus, covered in my previous article).
- Google (with their “vanilla” version of Android)
- LineageOS – an open-source version of Android
- /e/OS – a privacy-focused version of Android-based on LineageOS
The Results
I’ll quote directly from the conclusion:
With the notable exception of /e/OS, even when minimally configured and the handset is idle these vendor-customized Android variants transmit substantial amounts of information to the OS developer and also to third parties (Google, Microsoft, LinkedIn, Facebook, etc.) that have pre-installed system apps.
(Emphasis mine)
The concerns brought up in the research paper are numerous, but here are the main points.:
- Although AndroidOS allows a user to reset their advertising ID (to prevent long-term tracking), all the tested phones (with the exception of LineageOS and /e/OS) transmit device identifiers with the user data. This makes re-linking the new advertiser ID with the same device trivial. As the researchers put it, “[t]his largely undermines the use of user-resettable advertising identifiers.”
- For most phones, data is sent out to numerous groups. Samsung phones, for example, send data to Google, to Samsung, and to Microsoft. Huawei phones send data to Google, Huawei, Daily Motion, Avast, Qihoo 360, and Microsoft. LineageOS only sends data to Google, and /e/OS sends out essentially no data. You can see a list of the different types of data sent to different companies below:
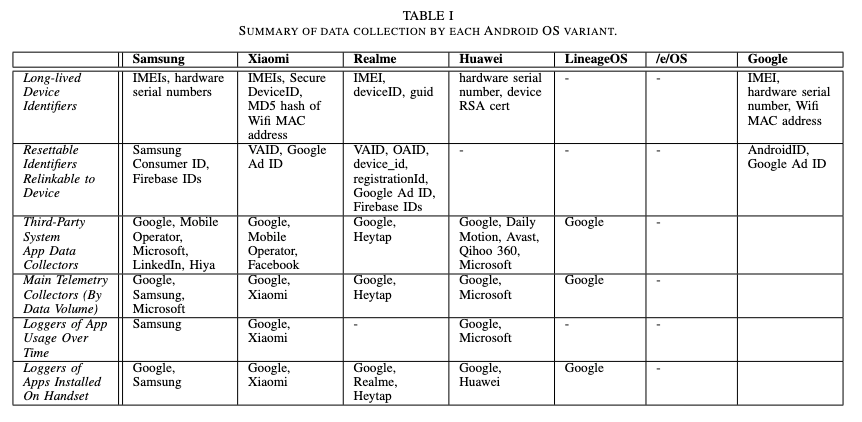
- The data sent includes things like user interaction (what apps are used, when are they used, how long are they used), when the user was on the phone or sending a text, the apps currently installed, and other usage details.
- There is no opt-out for this collection. In the research, all phones were set up with all optional privacy features disabled. However, this data was still collected and sent.
Final Thoughts
I posted a blog article about a similar research paper in April of this year.
That paper compared the data collection done by Google (on a Pixel phone) with the data collected by Apple (on an iPhone). From that research paper’s conclusion:
We find that even when minimally configured and the handset is idle both iOS and Google Android share data with Apple/Google on average every 4.5 mins. The phone IMEI, hardware serial number, SIM serial number and IMSI, handset phone number, etc are shared with Apple and Google. Both iOS and Google Android transmit telemetry, despite the user explicitly opting out of this. We find that even when minimally configured and the handset is idle both iOS and Google Android share data with Apple/Google on average every 4.5 mins. The phone IMEI, hardware serial number, SIM serial number and IMSI, handset phone number, etc are shared with Apple and Google. Both iOS and Google Android transmit telemetry, despite the user explicitly opting out of this.
As I’ve mentioned several times before, the data collection – to varying degrees – will always be present. The most important consideration for the end-user is: do you trust the company you are giving the data to?
With Apple the vast majority of the data goes directly to them, with non-Google Android phones, it seems like the data is scattered all across the internet. I think this consideration is far more important than if the data is collected at all.


Leave a Reply
You must be logged in to post a comment.