One of the recurring themes that keep coming back on this blog is the ever-increasing need for basic security practices from anyone who browses the internet.
The need for basic security practices applies double to anyone responsible for network equipment. And since almost every home has at least one Internet router (and sometimes several), this means that non-technical users are increasingly responsible for their own security.
While this blog does attempt to keep my regular readers up-to-date on major security stories or vulnerabilities (like my posts about the latest LastPass breach, the state of WordPress security, home router vulnerabilities, etc.) a new resource from the US’s National Security Agency provides some excellent and easy-to-implement advice on how to secure your home (and work) network against the most common attacks.
NSA Cybersecurity Information Sheet
First things first – you can find the 9-page document at https://media.defense.gov/2023/Feb/22/2003165170/-1/-1/0/CSI_BEST_PRACTICES_FOR_SECURING_YOUR_HOME_NETWORK.PDF.
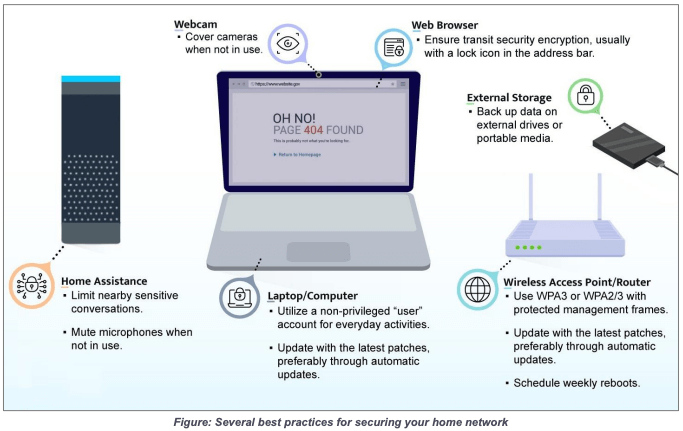
Go ahead and download it and take a look at it – while it does have some networking jargon, the first page has a descriptive executive summary and an image that gives you several of the most important security practices to make sure that you are implementing.
The Basics
A portion of the executive summary gives the three biggest behaviors to implement immediately:
- Upgrade and update all equipment and software regularly, including routing devices
- Exercise secure habits by backing up your data and disconnecting devices when connections are not needed
- Limit administration to the internal network only
The image gives you 10 additional specific ways to limit the vulnerability of computers, routers, and voice assistant devices:

Specifics for All Devices
Going further down the document, you get even more specifics about best security practices for individual devices. Some of the more important ones include the following:
- Upgrade to a modern operating system and keep it up-to-date: While you may not want the newest Windows, MacOS, or Linux distro, you are running a real, tangible risk by staying on unsupported software. When (not if) vulnerabilities are found in old software they are rarely patched (and sometimes never even announced), and often trivially easy to exploit.
- Secure routing devices and keep them up-to-date: This goes hand-in-hand with updating your OS. You should also look for a manufacturer that will support routers for a long time. A vulnerability here exposes all your devices to the public internet.
- Protect passwords: This goes without saying – make sure you are using a password manager (but probably not LastPass).
- Safeguard against eavesdropping: The NSA reminds you that if you have a voice assistant, they are always listening unless you push the “mute” button. If you don’t want them to be actively listening, either mute them or unplug them.
- Exercise secure user habits: Back up your devices frequently (and disconnect the backups to protect from ransomware), avoid connecting devices to public charging stations, leave computers in “sleep” mode to allow them to update automatically, disconnect network connectivity if devices are not used for an extended period.
- Take precautions on social networks: Avoid posting personal information that could be a security risk, avoid clicking unsolicited links, or accepting friend requests from unknown people.
- Exercise caution when accessing public hotspots: The security of a coffee shop or hotel hotspot is unknown (and likely not good). If you must use these hotspots, use a VPN and make sure to carefully monitor your devices.
There are also more advanced (but still good) best practices given, like implementing WPA3 or WPA2/3 on your router, wireless network segmentation (separating primary, guest, and IOT Wifi networks), setting up a router firewall, and limiting router administration to only internal networks.
The document does not tell you how to implement these specific best practices, but a quick Google (or DuckDuckGo) search with your specific device or software, along with whatever feature you’re trying to implement, will give you the instructions you need.

Leave a Reply